
Cybersecurity Guide 2025: Zero Trust Architecture in 90 Days
Implementing a Zero Trust Architecture (ZTA) is crucial for modern cybersecurity, and this guide provides a roadmap for organizations to adopt ZTA principles effectively within a 90-day timeframe, enhancing their security posture against evolving threats in 2025. Is your organization ready to face the cybersecurity challenges of 2025? The threat landscape is constantly evolving, demanding […]

Reduce Phishing Success by 40% with Multi-Factor Authentication
Multi-factor authentication (MFA) significantly reduces the success rate of phishing attacks by adding extra layers of security beyond just a password, making it substantially harder for attackers to gain unauthorized access even if they obtain a user’s credentials. In today’s digital landscape, phishing attacks remain a persistent and evolving threat to individuals and organizations alike. […]

NIST Cybersecurity Framework: A 6-Step Implementation Guide
The NIST Cybersecurity Framework (CSF) is a voluntary framework that provides a structured approach for organizations in the US to manage and reduce cybersecurity risks by understanding, assessing, and improving their cybersecurity posture through a set of standards, guidelines, and best practices. In today’s digital landscape, robust cybersecurity measures are essential for protecting sensitive data […]

Cybersecurity Guide: Top 5 EDR Solutions for 2025
The Cybersecurity Guide: Top 5 Endpoint Detection and Response (EDR) Solutions Compared for 2025 provides an in-depth analysis of leading EDR solutions, evaluating their capabilities in threat detection, incident response, and overall security posture to help organizations make informed decisions. In today’s complex threat landscape, having robust endpoint protection is crucial. This Cybersecurity Guide: Top […]

Cybersecurity Guide: Ransomware Attack Protection & Recovery
Cybersecurity Guide: Protecting Against Ransomware Attacks: A Step-by-Step Recovery Plan offers a comprehensive approach to understanding, preventing, and recovering from ransomware attacks, focusing on proactive security measures and a structured incident response strategy for businesses and individuals. Ransomware attacks are a growing threat, capable of crippling businesses and causing significant financial and reputational damage. This […]

Cybersecurity Guide: Securing Remote Workforces with VPNs in 2025
The “Cybersecurity Guide: Securing Remote Workforces with Updated VPN Protocols in 2025” explores updated VPN protocols, robust authentication methods, advanced threat detection, and cybersecurity awareness programs to ensure comprehensive protection for remote workforces. In 2025, securing remote workforces requires a proactive and adaptive approach. This Cybersecurity Guide: Securing Remote Workforces with Updated VPN Protocols in […]

Cybersecurity Guide: Data Encryption for Ultimate Security in 2025
Data encryption is a crucial cybersecurity measure for securing sensitive information in 2025, involving encoding data to prevent unauthorized access and maintain confidentiality, integrity, and availability. In today’s digital world, protecting sensitive information is more critical than ever. This Cybersecurity Guide: The Ultimate Guide to Data Encryption: Securing Sensitive Information in 2025 will provide you […]

Cybersecurity Awareness Training: Reduce Human Error by 25%
Cybersecurity awareness training is crucial for reducing human error, which is a significant factor in security breaches; effective training programs can lower human-related risks by up to 25% by educating employees about threats and best practices. In today’s digital landscape, human error remains a significant vulnerability in cybersecurity. A comprehensive cybersecurity guide: security awareness training: […]
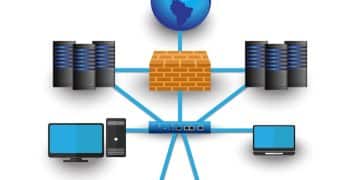
Network Segmentation: A Cybersecurity Guide for Enhanced Security
Network segmentation divides a network into smaller, more manageable segments, enhancing security by isolating critical assets and limiting the impact of potential cyberattacks, thus providing a robust defense strategy. In today’s digital landscape, cybersecurity threats are constantly evolving. One effective strategy for protecting your network is network segmentation, a technique that divides your network into […]

Mobile Device Security: A Comprehensive Cybersecurity Guide
Mobile device security is crucial for safeguarding company data, requiring a comprehensive approach that includes policies, employee training, and robust security measures to protect against evolving cyber threats. In today’s interconnected world, mobile devices have become indispensable tools for employees, enabling productivity and collaboration on the go. However, this convenience comes with significant cybersecurity risks. […]